The Mobile Platform Work Group (MPWG) is a TCG Technical WG that develops specifications and reference documents. The Trusted Mobility Solutions Work Group (TMS) is a TCG Solutions WG that develops use cases, frameworks, and other reference documents. MPWG and TMS collaborate frequently to address the evolving challenges of the mobile device markets around the world.
The Mobile Platform Work Group (MPWG) promotes the implementation of TCG technologies in mobile devices to support the wide variety of business models in consumer, enterprise, government, and academic environments. MPWG defines specifications and recommendations for trustworthy mobile devices that address the resource constraints of mobile devices (e.g., intermittent connectivity and limited battery life). MPWG collaborates closely with Global Platform and has co-developed recommended best practices for the use of Trusted Execution Environment (TEE) and other Global Platform technologies in trusted mobile devices.
The Trusted Mobility Solutions (TMS) Work Group promotes the adoption of TCG technologies within end-to-end solutions for mobile devices, telecom infrastructure, and enterprise networks. Mobile devices should include trustworthy device identity, strong authentication, device integrity, secure storage, and virtualization. In enterprise networks, mobile devices should also include policy-based access control, and application and data isolation mechanisms. TMS collaborates closely with Global Platform (secure computing), Mobey Forum (mobile banking), European Telecommunications Standards Institute (ETSI, network function virtualization and security), Open Mobile Alliance (OMA, device provisioning), and other standards bodies.
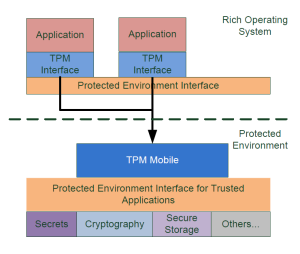
Figure 1 – Graphic: Example Architecture of a Protected Environment running a TPM Mobile
TPM 2.0 Mobile Reference Architecture: This specification defines an architecture for the implementation of a TPM 2.0 executing within a Protected Environment (in mobile platforms). It includes informative examples of several implementation approaches.
TPM 2.0 Mobile Common Profile: This specification defines a profile of the TPM 2.0 Library Specification applicable to all mobile devices that conform to the TPM 2.0 Mobile Reference Architecture that is optimized for ease-of-implementation in feature phones, basic phones, eBook readers, and other similar constrained mobile devices.
TPM 2.0 Mobile Command Response Buffer Interface: This specification defines an interface between a TPM and software and is intended to work with a large number of hardware implementation options, including a discrete TPM on a peripheral bus or firmware TPM in a Protected Environment as defined in the Mobile Reference Architecture. The Mobile CRB Interface can be implemented on any platform architecture, including PC Client systems.
TMS Use Cases – Bring Your Own Device (BYOD): This reference document considers a broad range of scenarios where TCG technologies can be applied in mobile device ecosystems.
The Mobile Platform and TMS work groups develop standards, implementation guidelines, use cases, and solutions that integrate core TCG technologies (including TPM, TNC, and SED) into mobile devices, telecom infrastructure, and enterprise networks to enable support for trusted computing in critical mobile applications such as mobile banking, health care, and distributed computing. MPWG and TMS actively reach out and collaborate with external standards bodies to include explicit requirements for TCG technologies in international security and mobile standards. MPWG has been active since TCG was founded and TMS has been active for over five years.
Bo Bjerrum is a Security Domain Architect at Intel. Bo has contributed to the Mobile Platform Work Group since 2013 and became a MPWG Work Group co-chair in 2015. Bo has been working with mobile platform security for years in multiple companies. During his carrier, he has defined security solutions for platforms, which span from pure modem, entry phones to more advantage devices like feature or smartphones.
Kathleen is a member of the Senior Professional Staff in APL’s Asymmetric Operations Department. Kathleen has contributed to the TCG Mobile Platform Work Group since 2011, became a MPWG Work Group co-chair in 2015, and is a lead editor. Her research at APL focuses on dynamic integrity measurement and trusted computing technologies for of desktop, server, and mobile platforms.
Alec is Manager of Security Standardization at InterDigital Communications, LLC. Alec has contributed to the TCG Trusted Mobility Solutions (TMS) and Mobile Platform Work Groups since 2011, became a TMS Work Group co-chair in 2014, and received a TCG Key Contributor award in 2015. Alec has extensive experience in standards development, security and privacy, system design, and applications development for major telecom operators and equipment vendors. Alec negotiated strategic TCG formal liaisons with European Telecommunications Standards Institute (ETSI) and Open Mobile Alliance (OMA). He is an active contributor in 3GPP SA3 (security) and ETSI NFV SEC (security). In the past, Alec served as co-chair of the IETF SPIRITS Working Group. Alec is an IEEE Senior Member active in the IEEE Communication Society and holds multiple US and international patents.
Carlin Covey is a Principal Engineer in NXP’s Security Technology Center, focusing on hardware support for trust architectures. Carlin has contributed to the TCG Trusted Mobility Solutions (TMS) and Mobile Platform Work Groups since 2011, became a TMS Work Group co-chair in 2013, and is a lead editor in both Mobile work groups. Carlin has been active in security engineering for over 30 years, serving as a System Architect for multiple government and commercial hardware/software security systems. He was a technical contributor for Open Mobile Terminal Platform, PKI Forum and IETF PKIX. He holds 10 patents on security-related innovations.
Ira is founder and President of High North Inc, a consulting firm that specializes in network software design, security and privacy, network management, internationalization, mobile devices, embedded devices, automotive security, and printing systems. Ira has been a TCG Invited Expert since 2008. Ira has contributed to the Trusted Mobility Solutions (TMS) and Mobile Platform Work Groups since 2011, co-founded and has co-chaired the TMS Work Group since 2011, and received a TCG Key Contributor award in 2015. Ira is a lead editor in Trusted Network Communications (TNC), Embedded Systems (EmSys), Internet of Things (IoT), Network Equipment, and other TCG work groups. Ira actively contributes to IETF, IEEE, Linux Foundation, DMTF, and SAE standards.
TCG Multiple Stakeholders Model
TPM 2.0 Mobile Specification Implementation Guidance
TCG Runtime Integrity Maintenance
Expand TMS UC v1 (BYOD) to all Enterprise mobile devices – collaborate with Open Mobile Alliance
Expand TMS UC v1 to add Mobile Banking and Mobile Payments – collaborate w/ Mobey Forum
Expand TMS UC v1 to add Network Functions Virtualization use cases – collaborate w/ ETSI NFV ISG