Authors: Seigo Kotani and Ira McDonald
A specification for providing hardware root of trust is evolving to serve the need to secure tomorrow’s automobiles.
Modern automotive vehicles rely on hundreds of sensors and electronic control units (ECUs) that may need to communicate through gateways with external systems such as a remote monitoring center at a manufacturer, a government traffic management system or various devices in the Internet of Things. The increasing complexity and connectivity to external networks make cars ever more vulnerable to attacks that could compromise passenger safety such as a hacker disrupting the steering controls of an automobile.
As software upgrades currently account for half of all automotive vehicle recalls, enabling and assuring secure remote vehicle software upgrades would be more convenient for consumers and less expensive for manufacturers than the hands-on approach most commonly used today.
Verification of the trustworthiness of all participating computing elements is central to meeting the connected automotive security requirements. A trusted system is one whose identity and integrity posture are assured and verified before that system is authorized to perform a specific function or to access or update specific information. A high level of trust can be affordably enabled by using a Trusted Computing Group’s Trusted Platform Module (TPM) to support a hardware-based root-of-trust.
TPMs already have expanded from use in PCs to many other devices, including hard disk drives, mobile phones and servers. The TCG recently formed a working group for embedded systems to develop specifications for using TPMs in very demanding environments such as automotive vehicles, network equipment and Internet of Things devices.
In April, TCG members Fujitsu and Toyota InfoTechnology Center presented a feasibility demonstration at the RSA Conference and the Society of Automotive Engineers International World Congress and Exhibition of successful mainstream automotive applications that leverage the TPM and the Trusted Network Communications specifications. These specifications are currently deployed in hundreds of millions of PCs, servers, tablets, phones and network equipment devices such as routers, switches and access points.
This approach can:
The TPM 2 Library specification allows for the definition of multiple platform TPM profiles. This sub-setting provides for cost-effective application-specific TPM implementations that will increase their ease of use.
TCG is developing specifications for two types of automotive TPMs, one for high-functionality and more complex applications, and the other for more lightweight applications that still require the root of trust- based capabilities.
The automotive-rich TPM specification and its anticipated implementation are targeted for use in a head unit or communications gateway with all the capabilities required to securely communicate directly with the public Internet. The existing automotive-thin TPM specification satisfies basic hardware root-of-trust needs, but has significantly fewer capabilities since it is intended to function as a security enabler within resource constraints of most current automotive ECUs.
Potential design characteristics for the future automotive-rich TPM include:
Compatibility with existing vehicle management applications that communicate with a remote maintenance center for vehicle safety and maintenance.
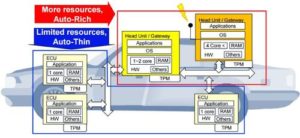
The TCG offers thin and rich approaches to automotive security.
The Fujitsu and Toyota InfoTechnology Center feasibility demonstration for the TCG auto-rich and auto-thin TPM concepts was recently shared at the SAE World Congress 2015.
For its part, the TCG recently contributed a response to the U.S. National Highway Traffic Safety Administration’s Automotive Electronic Control Systems Safety and Security note. It is also collaborating with the International Telecommunication Union Telecommunication Standardization Sector SG17, which is addressing secure software updates to automotive vehicles. The TPM 2.0 Library Specification also has been approved as an ISO/IEC International Standard.
–Seigo Kotani is a senior expert at Fujitsu Laboratories and co-chair of the Embedded Systems working group in the TCG. Co-author Ira McDonald is a network software architect at High North Inc, and co-chair of the TCG’s Trusted Mobility Solutions working group.
To read the full article, please click here.

Membership in the Trusted Computing Group is your key to participating with fellow industry stakeholders in the quest to develop and promote trusted computing technologies.

Standards-based Trusted Computing technologies developed by TCG members now are deployed in enterprise systems, storage systems, networks, embedded systems, and mobile devices and can help secure cloud computing and virtualized systems.

Trusted Computing Group announced that its TPM 2.0 (Trusted Platform Module) Library Specification was approved as a formal international standard under ISO/IEC (the International Organization for Standardization and the International Electrotechnical Commission). TCG has 90+ specifications and guidance documents to help build a trusted computing environment.