Wired.com recently published a frightening account of how a typical automobile can be hacked and controlled (more here at http://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/). In the test, a reporter in a late model Jeep experienced a series of events in which various functions performed oddly. The reporter notes that a group of hackers proved they “…can target Jeep Cherokees and give the attacker wireless control, via the Internet, to any of thousands of vehicles. Their code is an automaker’s nightmare: software that lets hackers send commands through the Jeep’s entertainment system to its dashboard functions, steering, brakes, and transmission, all from a laptop that may be across the country.”
While most in the security community and some in the auto industry are not all surprised by this, the question is what as an industry are we going to do about it? Even as auto makers like Tesla push ahead with remote software updates and self-driving cars become a reality even before regulations are in place (http://www.wsj.com/articles/googles-self-driving-cars-hit-regulatory-traffic-1426717776), security holes and the potential for attacks abound.
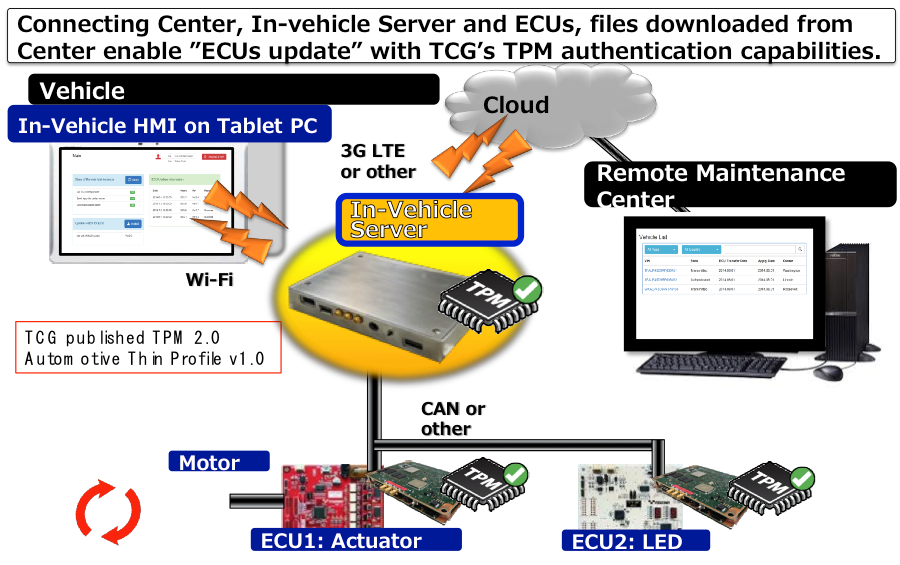
Trusted Computing Group has already tackled this issue in its Embedded Systems Work Group, which has a dedicated subgroup around vehicles. Just this spring, TCG, which also has been participating in SAE efforts around auto security, demonstrated how vehicle software can be updated securely and remotely, using trusted computing technologies that have already been widely vetted and deployed.
That demo, with input from TCG members including Fujitsu and the Toyota Info Technology Center, showed the secure update using the following steps:
1. Accurate remote determination of in-vehicle software and hardware configuration and integrity (via measurements performed using the TPM, securely attested by the TPM itself and verifiable by third parties, and transferred by TCG Trusted Network Connect (TNC) protocols)
2. Verification and logging of successful completion of intended software updates (via measurements performed using the TPM, securely attested by the TPM itself and verifiable by third parties, and transferred by TNC protocols)
3. Secure long-term storage of audit logs (created by the TPM itself) of the related update operations and TPM measurement operations (transferred by TNC protocols or secure system logging channels to network accessible self-encrypting drives (SEDs) or other high-reliability storage)
The demo shows key concepts of the recently published TCG TPM 2.0 Automotive Thin Profile.
While this use case does not cover all potential vulnerabilities in the vehicle, it’s a great start. And, this is one instance in which security can actually save money: some 50 percent of auto recalls are software-related, and the costs to manufacturers for updating software at the dealer starts at about $150 U.S. per vehicle. Millions of cars=a lot of potential savings.
For the complete demo description and FAQ, see http://www.trustedcomputinggroup.org/media_room/events/189.

Membership in the Trusted Computing Group is your key to participating with fellow industry stakeholders in the quest to develop and promote trusted computing technologies.

Standards-based Trusted Computing technologies developed by TCG members now are deployed in enterprise systems, storage systems, networks, embedded systems, and mobile devices and can help secure cloud computing and virtualized systems.

Trusted Computing Group announced that its TPM 2.0 (Trusted Platform Module) Library Specification was approved as a formal international standard under ISO/IEC (the International Organization for Standardization and the International Electrotechnical Commission). TCG has 90+ specifications and guidance documents to help build a trusted computing environment.